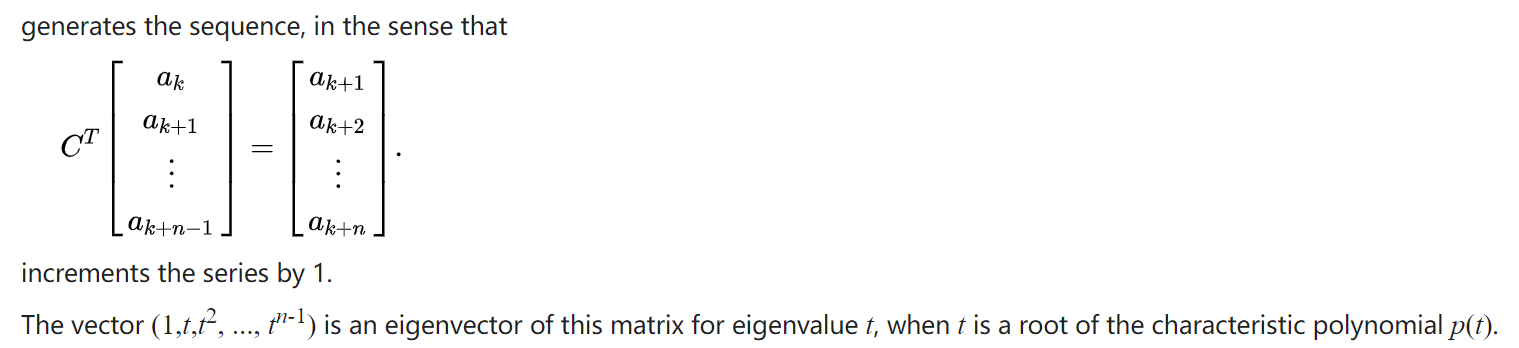
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
|
N = 43
m = 9
plain = [[30, 0, 41, 24], [37, 6, 8, 20], [12, 19, 24, 31], [33, 10, 42, 19], [22, 26, 40, 38], [32, 20, 35, 20], [31, 3, 39, 20], [26, 6, 0, 26], [25, 21, 32, 28], [9, 33, 37, 26], [13, 19, 20, 28], [34, 5, 12, 37], [11, 22, 18, 35], [37, 1, 2, 15], [33, 14, 15, 28], [7, 39, 34, 39], [8, 12, 1, 29], [18, 27, 9, 30], [7, 5, 1, 41], [31, 7, 28, 20], [33, 36, 8, 16], [23, 15, 15, 2], [41, 2, 29, 17], [1, 9, 22, 19], [14, 8, 15, 13], [37, 23, 34, 34], [16, 29, 37, 25], [39, 9, 24, 27], [20, 41, 18, 14], [6, 8, 30, 6], [16, 36, 38, 1], [40, 24, 40, 9], [13, 23, 41, 11], [5, 8, 19, 17], [30, 31, 4, 6], [4, 11, 23, 40], [37, 27, 18, 20], [41, 18, 7, 25], [17, 18, 25, 11], [25, 28, 41, 37], [33, 23, 0, 23], [20, 26, 10, 35], [20, 20, 28, 22], [31, 23, 32, 20], [2, 37, 13, 40], [26, 1, 37, 27], [7, 35, 9, 38], [30, 15, 41, 18], [25, 11, 31, 19], [35, 35, 33, 29], [33, 34, 35, 41], [3, 14, 16, 38], [42, 19, 32, 19], [6, 8, 42, 20], [8, 8, 10, 3], [33, 10, 22, 34], [10, 4, 1, 21], [39, 15, 24, 27], [38, 24, 22, 20], [2, 21, 32, 39], [14, 14, 11, 24], [18, 16, 29, 41], [28, 6, 19, 37], [3, 12, 6, 35], [25, 40, 6, 39], [5, 22, 40, 42], [39, 24, 5, 31], [14, 37, 5, 7], [36, 9, 31, 5], [28, 9, 8, 6], [36, 12, 32, 36], [28, 37, 16, 29], [20, 39, 42, 3], [15, 36, 38, 20], [12, 31, 27, 3], [27, 14, 33, 28], [26, 19, 8, 23], [6, 17, 17, 17], [2, 42, 0, 3], [0, 4, 8, 23], [12, 5, 33, 38], [23, 38, 30, 24], [1, 42, 15, 23], [17, 37, 27, 25], [24, 12, 18, 33], [20, 20, 26, 41], [36, 13, 23, 42], [39, 18, 25, 41], [11, 29, 17, 14], [3, 4, 25, 12], [0, 12, 4, 0], [27, 40, 37, 10], [30, 7, 13, 29], [16, 26, 36, 23], [31, 19, 10, 12], [4, 13, 10, 38], [14, 11, 19, 7], [37, 40, 9, 5], [1, 7, 30, 17], [37, 28, 20, 28], [35, 28, 34, 23], [7, 18, 33, 24], [21, 17, 15, 14], [29, 35, 15, 41], [30, 16, 13, 26], [39, 22, 34, 30], [5, 31, 22, 2], [41, 38, 37, 12], [40, 23, 19, 39], [28, 5, 27, 5], [20, 34, 22, 31], [3, 34, 6, 31], [42, 20, 13, 19], [24, 18, 23, 1], [27, 10, 20, 38], [22, 40, 37, 23], [17, 31, 5, 14], [7, 8, 16, 4], [14, 38, 5, 14], [41, 1, 13, 8], [6, 16, 35, 9], [26, 27, 13, 29], [30, 8, 14, 8], [36, 4, 35, 0], [41, 35, 19, 24], [31, 39, 20, 15], [27, 40, 21, 22], [22, 11, 10, 39], [14, 25, 24, 33], [0, 4, 7, 6], [35, 41, 41, 28], [27, 27, 12, 34], [10, 17, 11, 40], [38, 1, 36, 38], [25, 37, 14, 41]]
cipher = [[11, 26, 12, 12], [33, 10, 42, 19], [9, 40, 31, 36], [12, 31, 27, 3], [36, 2, 19, 11], [27, 10, 30, 26], [25, 12, 9, 42], [6, 40, 18, 8], [14, 13, 26, 7], [36, 3, 19, 18], [9, 33, 37, 26], [10, 4, 1, 21], [18, 26, 6, 24], [7, 14, 36, 38], [16, 10, 28, 17], [37, 28, 20, 28], [39, 15, 8, 35], [6, 0, 42, 28], [26, 39, 12, 7], [41, 21, 6, 31], [28, 34, 25, 21], [35, 33, 34, 39], [24, 6, 26, 7], [24, 14, 33, 16], [4, 41, 7, 3], [31, 41, 5, 32], [34, 33, 32, 17], [6, 8, 7, 24], [38, 8, 2, 15], [14, 25, 37, 22], [18, 18, 27, 15], [19, 8, 4, 7], [16, 3, 0, 22], [27, 6, 24, 3], [31, 40, 15, 23], [6, 22, 23, 41], [12, 40, 40, 40], [11, 7, 6, 42], [24, 29, 16, 26], [35, 4, 32, 20], [8, 31, 32, 26], [5, 0, 19, 29], [4, 4, 40, 13], [4, 24, 28, 41], [31, 20, 1, 1], [36, 1, 1, 29], [9, 36, 29, 7], [22, 11, 10, 39], [13, 20, 35, 37], [35, 37, 39, 17], [40, 11, 38, 6], [15, 13, 32, 41], [7, 39, 34, 39], [30, 0, 3, 16], [11, 18, 40, 30], [23, 29, 38, 2], [8, 29, 18, 34], [39, 5, 37, 39], [26, 11, 38, 26], [9, 3, 6, 33], [20, 20, 28, 22], [35, 14, 6, 40], [42, 24, 27, 24], [29, 7, 42, 10], [20, 30, 26, 42], [9, 31, 38, 38], [42, 6, 12, 40], [13, 19, 20, 28], [14, 25, 24, 33], [13, 19, 42, 18], [42, 30, 17, 3], [16, 0, 20, 1], [37, 42, 22, 26], [13, 14, 10, 3], [20, 23, 2, 5], [28, 34, 29, 28], [36, 8, 0, 7], [17, 30, 4, 13], [24, 6, 21, 23], [13, 24, 42, 33], [40, 5, 39, 26], [18, 29, 4, 33], [34, 8, 30, 30], [39, 9, 24, 27], [3, 35, 25, 40], [12, 18, 24, 26], [40, 38, 29, 33], [1, 28, 34, 7], [16, 21, 22, 34], [17, 37, 27, 25], [21, 35, 11, 25], [19, 29, 27, 18], [7, 24, 34, 7], [6, 5, 22, 33], [19, 24, 30, 20], [39, 23, 38, 27], [31, 39, 35, 17], [30, 15, 41, 18], [27, 8, 42, 22], [42, 19, 32, 19], [32, 0, 7, 4], [22, 37, 42, 41], [34, 5, 12, 37], [16, 11, 37, 11], [24, 21, 15, 15], [10, 37, 22, 33], [4, 11, 30, 13], [19, 19, 1, 27], [13, 12, 21, 11], [11, 24, 31, 21], [12, 4, 35, 23], [26, 41, 10, 25], [38, 32, 5, 4], [42, 28, 23, 23], [39, 24, 5, 31], [27, 10, 20, 38], [14, 15, 12, 28], [18, 17, 9, 18], [6, 41, 42, 13], [29, 10, 38, 13], [0, 11, 29, 35], [42, 12, 38, 18], [14, 0, 17, 24], [29, 27, 41, 2], [40, 15, 15, 18], [0, 5, 12, 0], [16, 37, 10, 20], [19, 31, 36, 20], [15, 36, 38, 20], [10, 35, 30, 40], [20, 18, 33, 1], [14, 14, 11, 24], [9, 37, 6, 25], [33, 37, 17, 34], [2, 11, 16, 6]]
hash = 'fd1f241a4d3ff9fc25d1e2480baa8b0c3b5a4559'
tmp = []
pc = list(zip(plain, cipher))
for pci in pc:
for pcj in pc:
if pci[1] == pcj[0]:
tmp.append(pci)
circles = []
for tt in tmp:
circle = [tt]
for _ in range(len(tmp)):
c = circle[-1]
for t in tmp:
if c[1] == t[0]:
if t in circle:
break
circle.append(t)
circles.append(circle)
assert len(list(set([str(x) for x in flatten(circles, max_level=2)]))) == 27
def to_str(vz):
res = ''
for vi in vz[:-1]:
res += str(vi[0])
res += ' -> '
res += str(vz[-1][0])
res += ' -> '
res += str(vz[-1][1])
return res
for c in circles:
print(to_str(c))
print()
def getLambda(a, b):
return Integer(a).inverse_mod(43) * b % 43
lambdas = []
for c in circles:
for i in range(4):
lambdas.append(getLambda(c[0][0][i], c[0][1][i]))
lambdas = sorted(list(set(lambdas)))
assert len(lambdas) == 9
print(lambdas)
lambdas2 = []
for l in lambdas:
tmp = []
for i in range(1, 43):
if pow(i, 3*m, 43) == pow(l, 3, 43):
tmp.append(i)
lambdas2.append(tmp)
print(tmp)
print()
from hashlib import sha1
import itertools
F.<a> = GF(43)
R.<x> = PolynomialRing(F)
flags = 'MRCTF{%s}'
for lams in itertools.product(*lambdas2):
f = R(1)
for l in lams:
f *= R(x-l)
t = list(f)
t = [-ti % 43 for ti in t[:-1]]
flag = flags % sha1(str(t).encode()).hexdigest()
if sha1(flag.encode()).hexdigest() == hash:
print(flag)
break
|